Network workers must see it! Layer 2 loop inspection process: from identification to cure
Hey! Brothers!
Is the Internet taking a turn for the worse? Business is intermittent, the indicator lights on the device panel flash like a bar lightball in a crazy synchronized fashion, and the login device is stuck in doubt. Don't panic, it's probably a two-story ring road!
For more information, please scan the WhatsApp QR code below to contact customer service.

01 How does the hammer ring exist?
1. Traffic monitoring:
Just like checking the water meter to find the leak point, we knock the command on the device to display interface brief | include up, Look at port traffic: If a few ports suddenly increase traffic several times more than normal business volume, chances are that the ring road is running a broadcast storm. But if the traffic increases only slightly, or if the device turns on broadcast suppression, this may not be enough and another option is needed.
2. MAC address drift:
The MAC address should have been safely in a certain interface, and if it had ADHD like crazy "moving" between different interfaces, it was irrefutable evidence of the loop.
· Check the police first:
Display trapbuffer to see if there is MAC drift alarm (OID 1. 3. 6. 1. 4. 1. 2011. 5. 25. 160. 3. 7);
· Re-check the record:
First knock mac-address flapping detection open detection, and then usedisplay mac-address flapping recordLook at which MAC is wandering around, and the corresponding interface is the nest of the loop. (Note: occasional floating may be a small accident, but continuous floating is the real loop)
3. Loopback Detection:
· First global open detection: loopback-detect enable;
· Then to the specified VLAN "task": Interface view knock loopback-detect packet vlan vlan-id, the way to set the detection loop after the penalty measures (such as shutdown interface);
· Finally, use the display loopback-detect to see the results, which road is blocked at a glance.
(Warm Tip: This trick is a bit resource intensive, remember to shut it down when you use it!))
02 Break a loop operation
1. Breaking a Ring: Cut the pieces quickly and let the business live first!
When the ring road is tearing business to a grinding halt, don't waste words, go straight to:
· Step 1 : Figure out the network topology diagram
Just like you have to look at the blueprints before you defuse the bomb, and if you don't know where the loop is, you can make the network collapse.
· Step 2 : Pick a move that has the least impact
A. Kick the looped port out of the VLAN;
B. Direct shutdown of the loop port: simply cut off the loop;
C. Physical pulling: the most direct physical break, suitable for emergency.
· Step 3: Confirm operational revival
Broken ring quickly see the flow down, MAC address is not floating, business recovery is successful.
2. Long-term optimization: After the first aid, the root cause must be treated, otherwise the ring road may come back:
· Scenario 1: Put the network in environmental protection
If it's a physical loop that's causing the problem, deploy a spoofing protocol, likeSTP/RSTP/ MSTP ,It is equivalent to setting a one-way street for the network, so you will never have to worry about going in circles.
· Situation 2: Upgrade the hardware configuration of the physical link
o If the link quality is too poor, the protocol message is always stuck in the road, so decide to change the network cable / fiber to make the signal transmission smoother;
o If the bandwidth is not enough, the protocol messages are crowded out, and they are aggregated directly on the chain, and the bandwidth can be doubled and redundant, which stabilizes a batch.
03 These ring road scenes,
Old net workers have a headache when they see them!
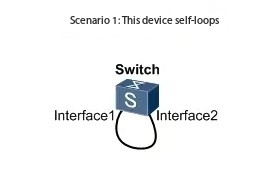
1. The device loops itself: it loops around itself
For example, one of the interfaces of the switch plugs itself, or the lower-connected network cable plugs the same device at both ends, a typical short-circuit operation.
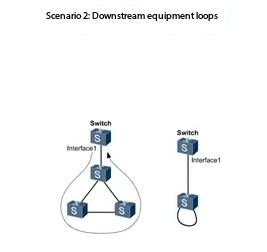
Downstream equipment ring road: boys dig holes and holes and big brothers
The access layer switch is not configured to break the protocol, and the PC or the camera is disorderly wiring, resulting in the loop infection from the downstream all the way up.
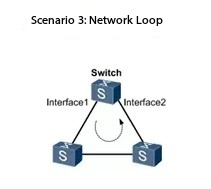
2. Network topology: poor planning, holes everywhere
Multiple links are misconnected between core layer / convergence layer devices, and STP is not opened, which directly forms a physical closed loop.
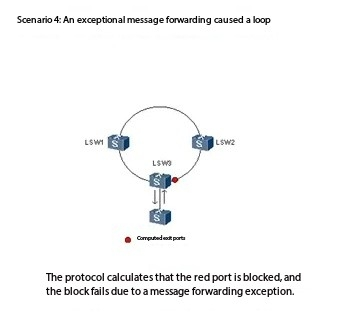
3. Message forwarding exception: software bug doing things
Switch forwarding logic, such as MAC address table error aging, resulting in messages in the infinite loop between devices, live around the loop.
For more Layer 2 loop resources, follow the Facebook account & youtube account: Thinkmo Dumps


