How easily can your network be compromised? ARP Flood Attack Revealed!
Good evening, my friends!
Let's do an experiment today called the ARP flood attack experiment, This experiment will cause a bandwidth drain on our network, and if it's a gateway-targeted attack, the ARP table settings on the gateway will overflow, leading to a significant drain on the device's performance. This does sound quite alarming, so let's go ahead and perform the experiment.
For more information, please scan the WhatsApp QR code below to contact customer service.

01 An Introduction to ARP Flooding Attacks
ARP (Address Resolution Protocol,Address Resolution Protocol (ARP) is a protocol that resolves the IP address to the corresponding MAC address. The ARP protocol has the advantage of being simple and easy to use, but because it has no security mechanism, it is easy to be used by attackers.
In the network , the common ARP attack methods include ARP spoofing attack and ARP flooding attack .
This article mainly explains ARP flooding attacks and how ARP flooding attacks are implemented.
ARP flooding attack: ARP flooding attack is a denial of service attack,Attackers send a large number of forged ARP request packets or free packets to the device whose destination IP addresses cannot be resolved, causing the ARP table entries on the device to overflow and unable to cache the ARP table entries of normal users, thus affecting the normal packet forwarding.
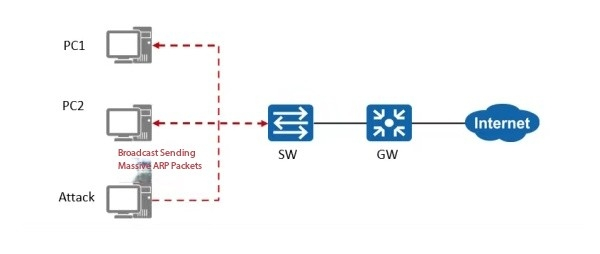
For example, in this image, the attacker intentionally sends a large number of useless ARP packets, and the entire broadcast domain is attacked, including PC1, PC2 and the gateway.
02 ARP Flooding Attack Experiment
Install a software called Core packet generator.
Then open Core packet generator as an administrator
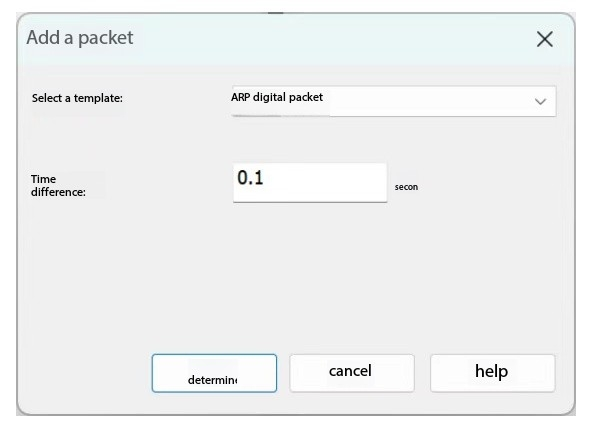
Add ARP digital packet
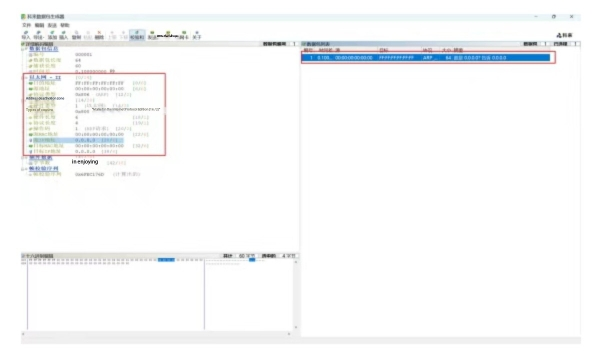
After adding, yes, we still need to do the content of the data packet.
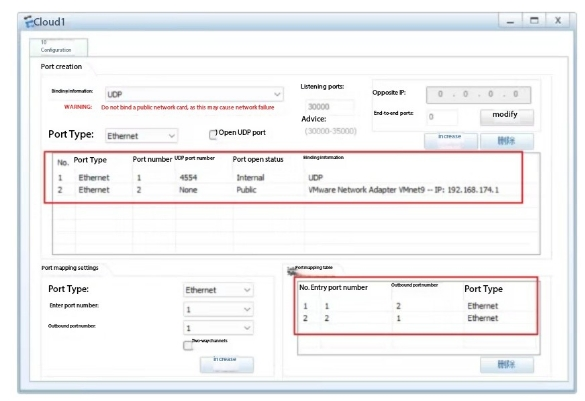
We bridge a network card and connect it to the ENSP emulator.
We need to know what an ARP packet really looks like.
In a network, a network segment communicates between pieces of the network. For example, PC1 configured at 192.168.109.10 accesses PC2 at 192.168.19.20. Because PC1 does not initially have an ARP mapping table, it sends an ARP request to the broadcast domain.
The composition of the newspaper is shown here:
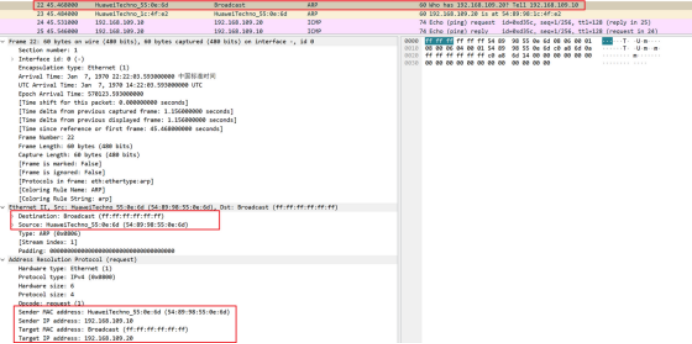
In the frame format, we are the source MAC is PC1 MAC address; Objective MAC is all F, ff: ff: ff: ff: ff: ff.
The content of the digital packet of the ARP is that the source MAC is the MAC address of the PC1; The source IP is the PC1 IP address 192.168.109.10; Objective MAC is all F, ff: ff: ff: ff: ff: ff; The destination address is PC2's IP address 192.168.109.20.
The learning of ARP table has nothing to do with the MAC address in the two-layer header, and records table entries based on the IP and MAC addresses in the ARP packet.
The above is the basic content of an ARP digital packet, after understanding the content of digital packet, we will construct the ARP digital packet.
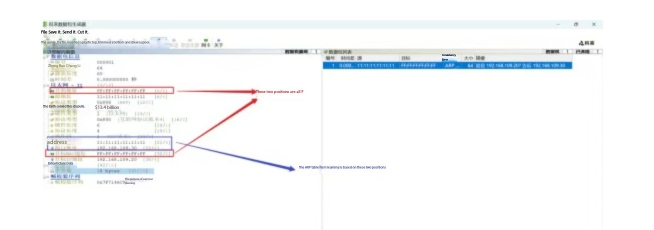
There is no ARP flood attack in an ARP packet , so let 's have a few more . It can be added or clicked to copy
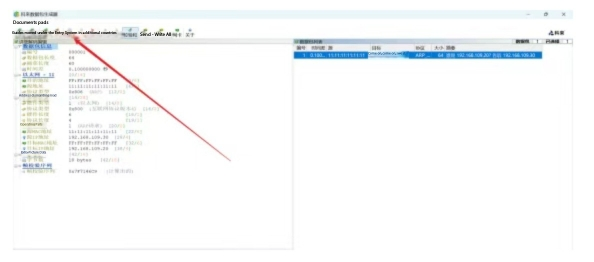
Then Paste
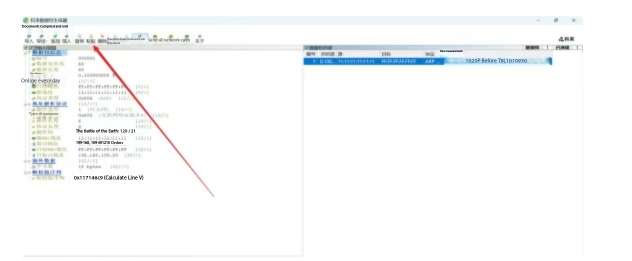
Only change the part that can record ARP table entries
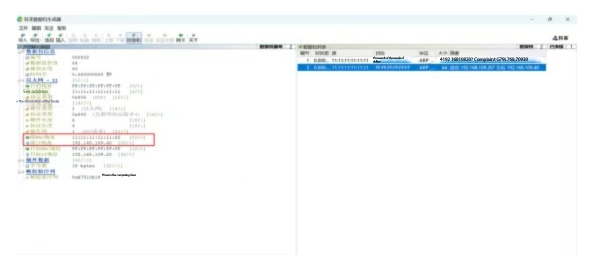
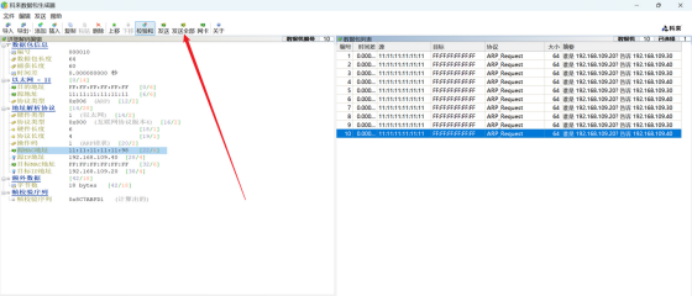
Likewise, we replicate many times, first completing ten, then clicking on the network card
Select the network card corresponding to the cloud set in ensp
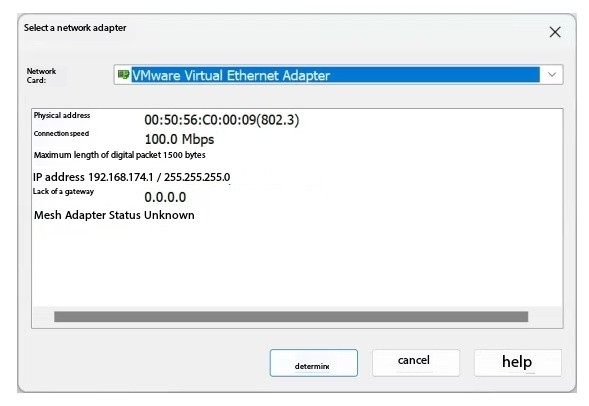
Then click to send all
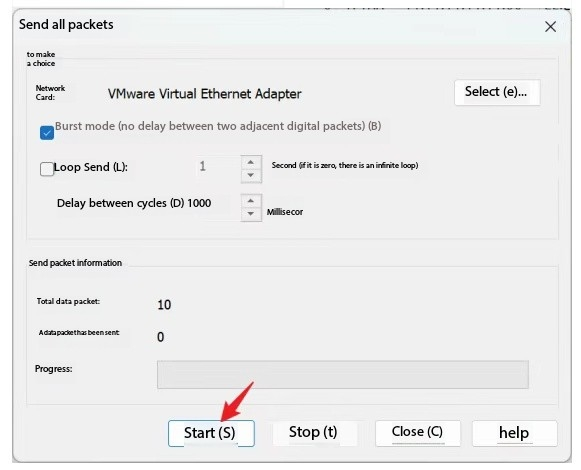
Then we are in the PC in ensp, can look at the arp map table
PC>arp -a
Internet Address | Physical Address | Type |
192.168.109.20 | 54-89-98-1C-4F-E2 | dynamic |
192.168.109.30 | 11-11-11-11-11-11 | dynamic |
192.168.109.40 | 11-11-11-11-11-22 | dynamic |
192.168.109.60 | 11-11-11-11-11-44 | dynamic |
192.168.109.50 | 11-11-11-11-11-33 | dynamic |
192.168.109.70 | 11-11-11-11-11-55 | dynamic |
192.168.109.90 | 11-11-11-11-11-77 | dynamic |
192.168.109.80 | 11-11-11-11-11-66 | dynamic |
192.168.109.110 | 11-11-11-11-11-77 | dynamic |
192.168.109.100 | 11-11-11-11-11-88 | dynamic |
192.168.109.120 | 11-11-11-11-11-98 | dynamic |
Because the request packet of ARP is a broadcast packet, the entire broadcast domain will be subject to ten useless ARP packets, including the gateway, and then count the ARP table entries, resulting in a waste of resources, so as long as enough is constructed, the resources of the ARP Table entries can be exhausted.
For more ARP resources, follow the Facebook account & youtube account: Thinkmo Dumps


