What is Port Security in a Switch? A Pack of Articles to Learn
Good evening, my friends!
Today we will talk about a practical security mechanism in Huawei switches - port security (Port Security) 。This is the first gatekeeper of the network access layer defense, especially in the office network, dormitory network, visitor area and other environments.
For more information, please scan the WhatsApp QR code below to contact customer service.

01 What is Port Security?
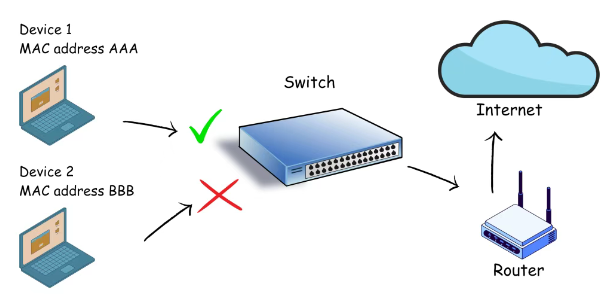
Port Security ( Port Security ) is a kind of access control mechanism based on MAC address filtering , which is used to prevent unauthorized terminal equipment from accessing the switch port .
When the port security function is enabled, the switch will learn,restrict, bind or block the MAC address of the interface to ensure the legitimacy of the access terminal.
02 Why Port Security?
In actual network operations, you may encounter these situations:
· Colleagues pull the notebook from a port to another location, MAC address change triggered a security alarm;
· Some users secretly add a switch / wireless AP to expand the port to access more devices;
· Attackers use tools to forge MAC addresses and insert network monitoring data;
· Internal threat actors carry out MAC FloodAttack that causes the switch to fail forwarding and causes data broadcast leakage.
When port security is enabled, you have these capabilities:
· Limit the number of access devices per port (e.g., up to 1MAC) ;
· Strong binding of certain MAC addresses , only fixed equipment access ;
· Detect and block illegal terminal access quickly ;
· Trace the source of attacks or violations , in conjunction with a log system .
03 How Port Security Works
The core of port security control is to learn and restrict MAC address 。Once enabled, the interface will no longer blindly learn all MAC addresses, but instead:
Category | Explanation | Is it ageable? | Is it configurable? |
Static MAC | Administrator manually binds | ❌ Not aging | ✅ Yes |
Dynamic MAC | Normal learning comes. | ✅ It can age | ❌ No |
Secure Dynamic MAC | Learn under port security | ✅ A cap on quantities may be set | ✅ Yes |
Sticky MAC (Sticky) | Automatically transition to static after dynamic learning | ❌ Not aging | ✅ Yes |
In addition , security policies can also define post-violation behavior :
Pattern | behavior | Scenarios suggested |
Protect | Discard illegal data frames without alerting | Suitable for scenarios with high availability requirements |
Restrict | Discard and alert, keep a log. | Suitable for risk screening |
error-down | Close the port directly | Suitable for situations with strong margins of safety, such as the finance department |
04 Configuration sample (Huawei switch)
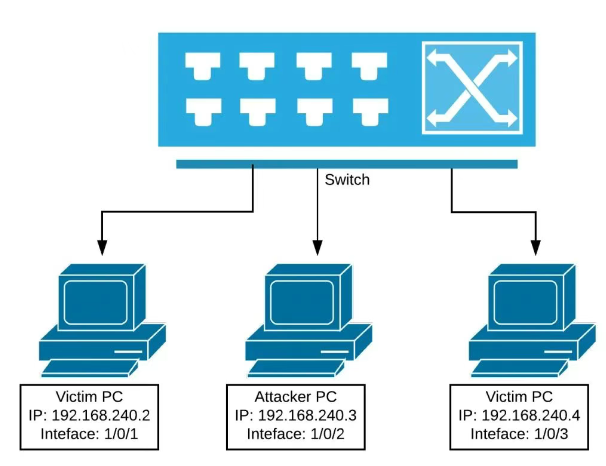
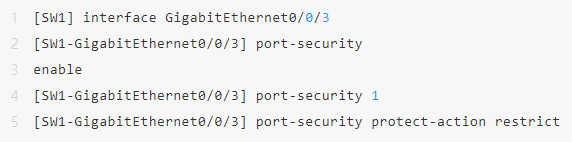
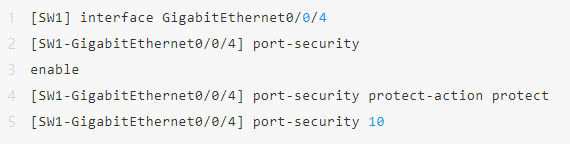
Scenarios Needs:
· SW1 access office terminal;
· Each port allows access to a maximum of 1 device;
· If an illegal MAC is detected, automatically close and alert;
· Automatically sticky learns the MAC address of the currently connected device.
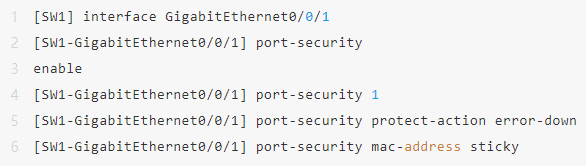
The sticky learning MAC address still exists after the device is rebooted, and is suitable for office, financial, printer and other terminals.
Scenarios Expanding Applications
Scenario 1: Bonding fixed asset equipment such as cameras
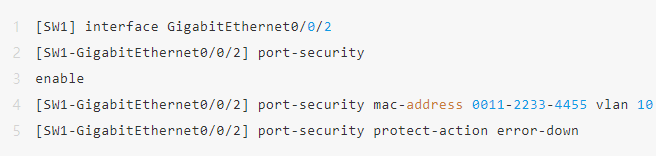
Scenario 2: dormitory / public area port, allowing only 1 device
Scenario 3: Visitor areas activate protection mode to prevent flooding
05 Verification commands and troubleshooting
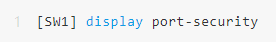
View port security status
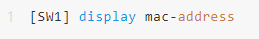
View the learned MAC address
Restore disabled port
Use advice and best practices
1. With 802.1X authentication or MAC authentication , build multi-layer access control strategy ;
2. Pay attention to the risk of device replacement when binding MAC address statically , sticky learning is more flexible ;
3. Log and alarm platform linkage , timely detection and handling of security incidents ;
4. Monitor the change of port security status , it is recommended to use NMS centralized management ;
5. Use error-down mode with caution , to avoid misoperation affecting normal business .
06 Attack and Defense Perspective: MAC Flood Attack Protection
The attacker uses tools to forge a large number of random MAC addresses to the switch, causing the switch MAC table to overflow, thus flooding traffic and monitoring other user data.
Port security can limit the maximum number of MAC addresses allowed to learn on a port, and trigger policies immediately when attack traffic exceeds the limit, forming effective protection.
That's all for today, port security is small, but it is the first line of defense for network security.Hope you don't ignore this useful function when deploying the switch.
If you find it useful, remember to share it!
For more Switch Port resources, follow the Facebook account&youtube account: Thinkmo Dumps


