What is the impact of a boundary gateway protocol on network security?
Good afternoon, students!
Today we are going to talk about a protocol that is very important for backbone network operation (BGP, Border Gateway Protocol) ,And what it has to do with cybersecurity.
BGP is the "routing master" of the Internet, which is responsible for the global autonomous system (AS) exchange of routing information。What appears to be a "low-level" protocol hides security risks.Today, we will take you to uncover its "security veil."
For more information, please scan the WhatsApp QR code below to contact customer service.

01 What is Border Gateway Protocol (BGP)?
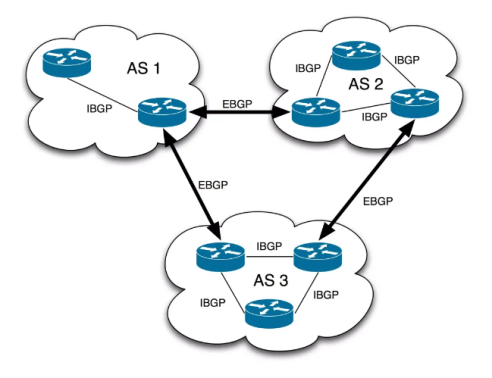
BGP is a path vector routing protocol, which is mainly used for routing information exchange (AS) between autonomous systems。Every ISP, enterprise, and even some large Internet companies have their own AS numbers and use BGP to interconnect.
For example : when you visit a foreign website , there may be multiple AS hops behind , and these paths are selected by BGP .
02 Problems and Challenges of BGP in Network Complexing Security
1 BGP Hijacking ( BGP Hijacking )
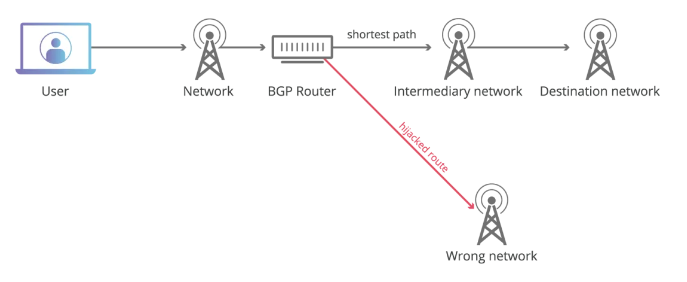
Attackers forge routing declarations, claiming "I own some IP" to intercept or redirect large amounts of traffic. Once successful, the consequences of such an attack are extremely serious and could result in:
· Data is intercepted or listened to;
· User access is interrupted or bypassed;
· Malicious content delivery ( such as DNS spoofing ) ;
Case in point : In 2018 , a Russian ISP mistakenly reported Google 's IP address , causing a large number of users to fail to access Google services .
2 BGP leaks (BGP Leak)
Routes that should be used internally are mistakenly posted to the public internet, potentially causing network-wide routing instability or even paralysis.
This is similar to accidentally sending internal company documents to WeChat Moments, which not only exposes privacy but may also cause a crisis of trust.
3 Lack of encryption and authentication mechanisms
The traditional BGP protocol itself does not have authentication mechanism and does not verify the identity of the other party by default. Unencrypted BGP sessions are vulnerable to hijacking or tampering by intermediaries.
03 So what do we do? - BGP Security Measures
UseTTL Security / GTSM limits the number of hops between BGP peers to prevent spoofing.
BGP MD5 / SHA Authentication Configures an authentication password for BGP sessions to prevent unauthorized connections .
Prefix / AS Path Filter configures the prefix filter strategy and path filter rules reasonably to prevent the abnormal routing.
The application of ROA and RPKI technology through the Resource Public Key Infrastructure ( RPKI ) verifies whether the route announcement comes from the legitimate holder to prevent BGP hijacking .
Black hole routing ( BGP Blackhole ) linkage with DDoS protection , quickly send black hole routing , reduce the impact of attack traffic .
04 Scenarios Expanding Applications
Scenario 1 : Enterprises connect with multiple operators to export BGP filtering rules to prevent local networks from being " hijacked " or used as attack platforms .
Scenario 2 : Network boundary of IDC / cloud service provider enables RPKI authentication and integrates with traffic cleaning platform to achieve real-time security linkage.
Scenario 3 : Research / education network interconnection with strict BGP policies to avoid routing errors affecting the entire network .
05 Verification and screening recommendations
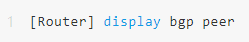
Check BGP Neighbor Status
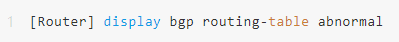
Identify sources of illegal routing
RPKI Validation Status Check
06 Use advice and best practices
· It is recommended to enable BGP authentication and AS-Path filtering on the exit router;
· Update the prefix list regularly to avoid expiration or mismatching;
· It is recommended to deploy RPKI to access the global verification system;
· Cooperate with logging platform to monitor BGP changes, quickly respond to exceptions;
· BGP priority and backup paths can be configured for critical business paths to improve redundancy.
Offensive and Defensive Perspectives: BGP Hijacking and Countermeasures
Targets of BGP hijacking are usually sensitive business traffic or used to expand the attack surface, such as to DNS servers delivering false responses。Using RPKI and strict policy filtering can effectively identify and reject illegal BGP announcements.
We shared this today. BGP is the "backbone" of the stable operation of the global mutual network and the "important town" of network security protection. Understanding how it works and the risks are a must for any network engineer!
For more BGP resources, follow the Facebook account&youtube account: Thinkmo Dumps


